How to Master the Evolving Challenges of Mobile Forensics

Dan Regard

Bobby Williams
May 28, 2025

Dan Regard is the President and CEO of Intelligent Discovery Solutions, Inc. (iDS). He helps companies solve legal disputes through the smart use of digital evidence. He is the author of “Fact Crashing™ Methodology” and is a contributing author to multiple other books on discovery and eDiscovery.
Bobby Williams is a Director at iDS. He is a forensic data testifying expert.
How to Master the Evolving Challenges of Mobile Forensics
This is the third article of a 10-part series on how technology is transforming evidence, litigation, and dispute resolution. In this installment, we’ll explore mobile forensics and how this area has changed due to increased privacy, increased security, and user habits. Here are the first and second stories in the series.
In today’s digital age, mobile forensics plays a vital role in legal and criminal investigations. Mobile devices store crucial personal and professional data relevant to legal disputes and criminal investigations. Extracting and analyzing this data presents numerous challenges, from encryption and privacy concerns to data volatility and device security features. Thankfully, there are evolving tools and techniques for recovering, authenticating, and presenting this evidence in litigation.
Let’s examine the current landscape of mobile forensics, the emerging methodologies in the field, and the ongoing challenges that legal and forensic experts face.
The Evolving Role of Mobile Data Forensics
Mobile device data has become a cornerstone of digital investigations. Whether in civil litigation, corporate internal investigations, or criminal proceedings, mobile forensics offers a direct window into user communications, location history, and application usage. Text messages, call records, emails, and social media interactions are often pivotal in establishing timelines, verifying alibis, or proving intent. Additionally, geolocation data and metadata embedded within digital files can provide context to events and actions, enhancing fact-finding in legal proceedings.
Here are three areas of mobile forensics that have been eye-opening to our team:
- Start with the Phone, But Don’t End There
When I first got into mobile forensics, the smartphone was the goal, the end target, the ultimate jackpot of data. Now we see it as the beginning of an investigation where threads emanate outwards toward other systems, cloud accounts, and connections. Do you have access to a phone? My first step is to look at the list of installed apps and browser history.
- You Can’t Always Get What You Want
To riff on the classic Rolling Stones’ lyric: “You can’t always get what you want. But if you try sometimes, well, you might find you get what you need”—unless you don’t. In that case, you need to look elsewhere.
For example, the iPhone now holds email in a special memory enclave. We cannot (currently) acquire email in bulk directly from the phone. You’re better off getting the user credentials and collecting from the “cloud.”
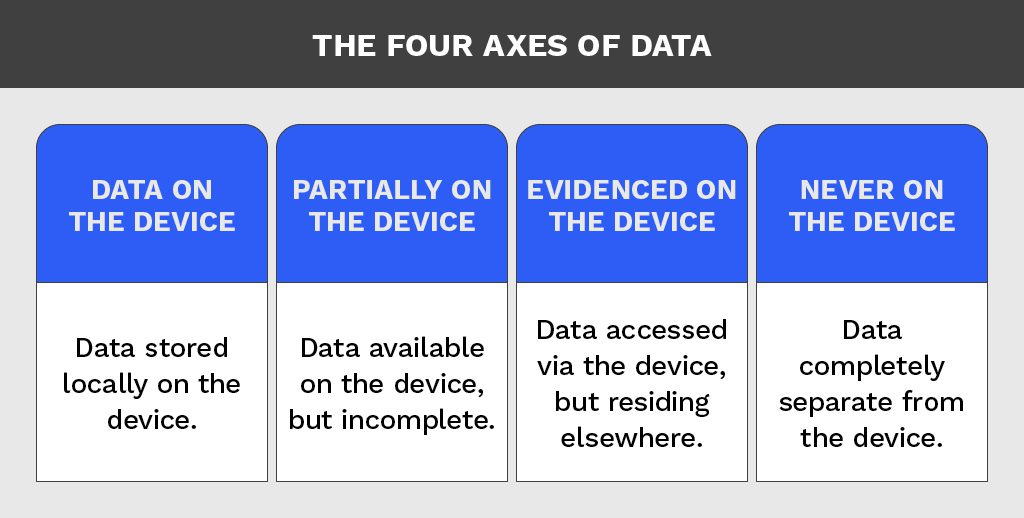
- Smartphones Have Four Axes of Data
That’s right. There are four axes of data associated with smartphones. Data that is on the device (and can be acquired). Data that is partially on the device (such as only 2 weeks of email). Data that is evidenced on the device but does not reside on the device (such as browser history). Data that was never on the device (such as phone carrier Customer Detail Records [CDRs]).
For these reasons, the mobile forensics investigative paradigm has shifted from “Follow the Phone” to “Follow the Data” whereby each type of data may need its own collection playbook.
Everything is Subject to Change
Oh, and as for the Caveat Lector – everything is subject to change. The data we can acquire, and from where we acquire it, can change on any given day due to updates in the operating system, the application, the user configuration, or the tools we use – where developers are constantly in a game of cat and mouse trying to pierce the protections and encryption that device makers are constantly strengthening.
For example, recently a client asked us to capture some specific Snapchat messages. Snapchat is designed to be ephemeral, meaning that snaps are meant to delete after a short period. However, under certain conditions, forensic tools can still recover this data. Sometimes.
For this client, we designed a multi-layered strategy:
- We performed a physical image acquisition of the smartphone—in this case an iPhone— and used Cellebrite to extract recoverable data from the Snapchat application.
- We went beyond the device and used the user credentials to perform a cloud-based collection via Oxygen Forensics, targeting Snapchat’s cloud-stored data.
- We then logged directly into the user account, and used Snapchat’s built in “Download My Data” feature to acquire the official data footprint.
- We then reverted back to the phone image and searched Photos for screenshots of Snapchat messages that may have been saved manually.
We then discussed, but decided not to pursue:
- iTunes backups of the iPhone
- The imaging and extraction of data from other connected devices
- Backups in the user’s iCloud account
- App-specific syncing to the user’s iCloud account
Snapchat is a great example of a multilayered approach to data-centric forensics. So, the next time you’re in an investigation, instead of thinking about the container, start thinking about the contents. Determine your case needs and build a plan from there.
Closing Thoughts: Join the Conversation
This is just one piece of the bigger conversation on the future of evidence. As legal professionals, we are relied upon to stay ahead of how emerging technologies impact investigations, case strategy, and courtroom advocacy. It’s important to partner with people who specialize in helping law firms, corporations, and regulators navigate the challenges of digital evidence—whether it’s mobile forensics, AI-generated data, or system logs that rewrite how we establish facts. Let’s continue the discussion.
Critical intelligence for general counsel
Stay on top of the latest news, solutions and best practices by reading Daily Updates from Today's General Counsel.
Get the free newsletter
Subscribe for news, insights and thought leadership curated for the law firm audience.